AWS - Cloud Security [chapter 0x1] - Identifying AWS Account ID from a public S3 - PWNEDLABS (Different Approach)
Hello world!
Background
Before we getting start with the content, I would like to mentioned that this post is originally come from the following (lab) created by pwnedlabs and this post is inspired from the following youtube video’s comment (link). The video itself is created by Afshan - AFS Hackers Academy you can also check it from this (link) and the original youtube comment also posted in this video.
So little bit of background of the lab, the lab itself taught you how to leverage a misconfigurate public s3 bucket that could lead to exposing AWS Account ID using tools such as s3-account-search. The lab gives you 2 options to do the task either using the access account and secret key that provide by the pwnedlabs or you can setup access account and secret key by yourself through your AWS account.
The first task is already cover by Afshan - AFS Hackers Academy. However, as I looking around the internet and some write up, I don’t find any blog that talk about the second option or it’s just me that not looking for it hard enough. Thus, in this post I will share it to you how to setup the IAM user that can be used to running s3-account-search.
Finally, let me also emphasize it again that knowing AWS Account ID is not consider a vulnerability nor a security flaw, however, as stated in the lab that knowing the account ID of an organization you are assessing the security of could be helpful for further analysis.
This post will be
Part 1 - IAM Setup
The first part is pretty straightforward as you need to create a IAM user that have sts:AssumeRole and S3 bucket policy which are s3:GetObject and s3:ListBucket. In this case, I created one new user named “leaky_user_bucket”, in this case I do not attached any permission or role yet, this will come later.
After that I create access key for this user
Next is to create two policies that I have mentioned earlier and attached this into the “leaky_user_bucket”
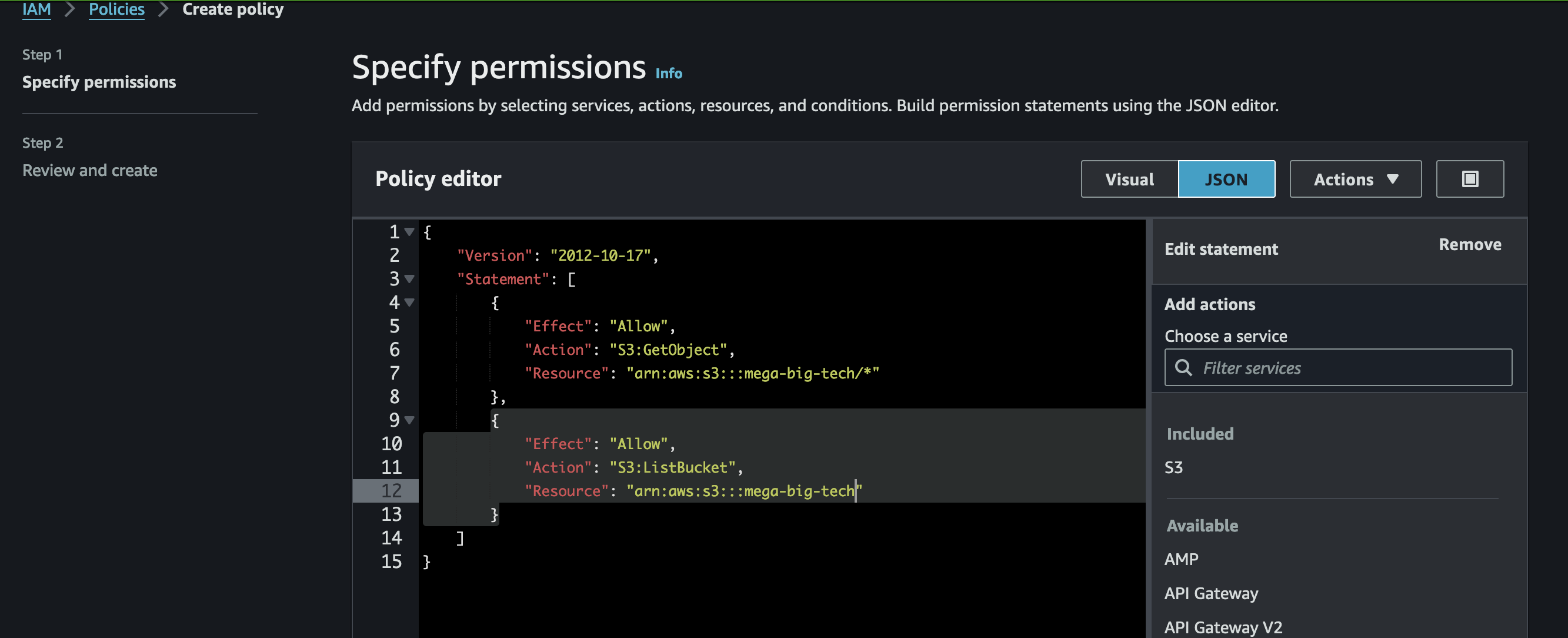
When creating the policy I just straight to specify permissions via JSON mode in policy editor
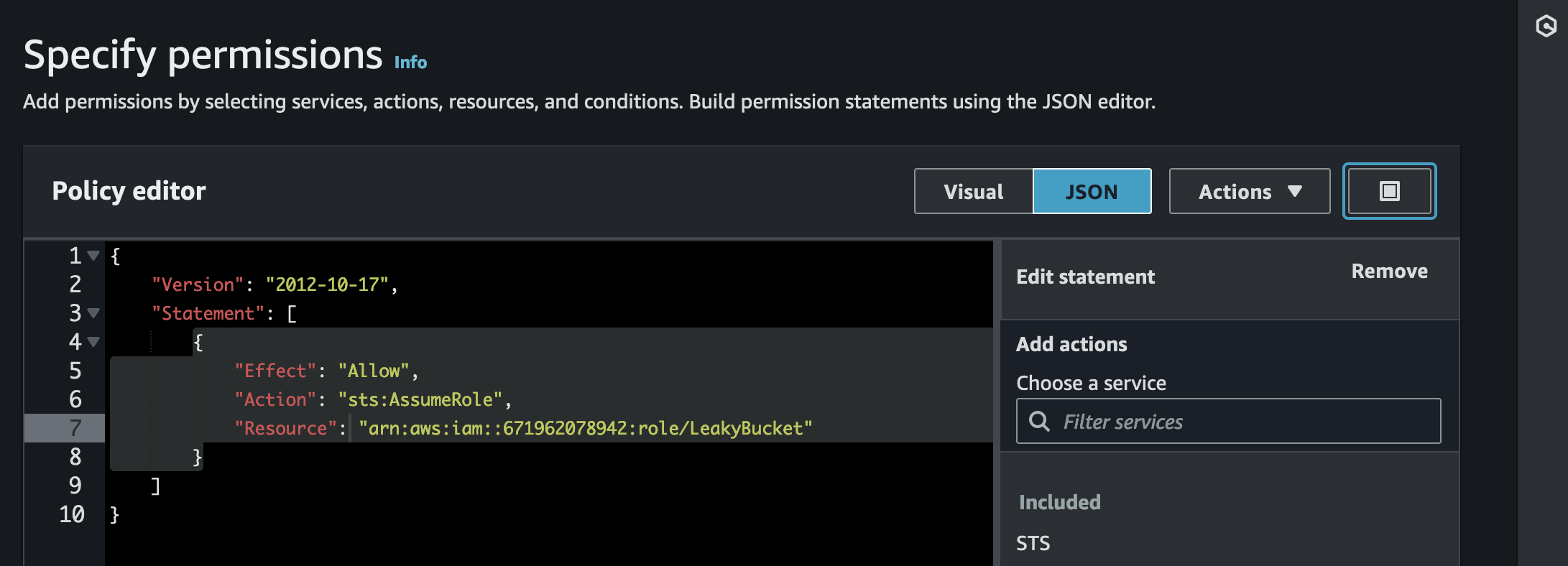
Put the following detail, I changed the aws account id based on the user “leaky_user_bucket” and for the role you can put any name but in this case I will put “LeakyBucket”
After that you saved and named the policy anything you want while in this case I put the policy name as “assume_role_policy_pwned”. Finally you create the S3 bucket policy like this:
Again for the naming you can choose anything you want while in this case I put the name as “mega_big_bucket_leak”. At the end of this part you will have two policies like this:
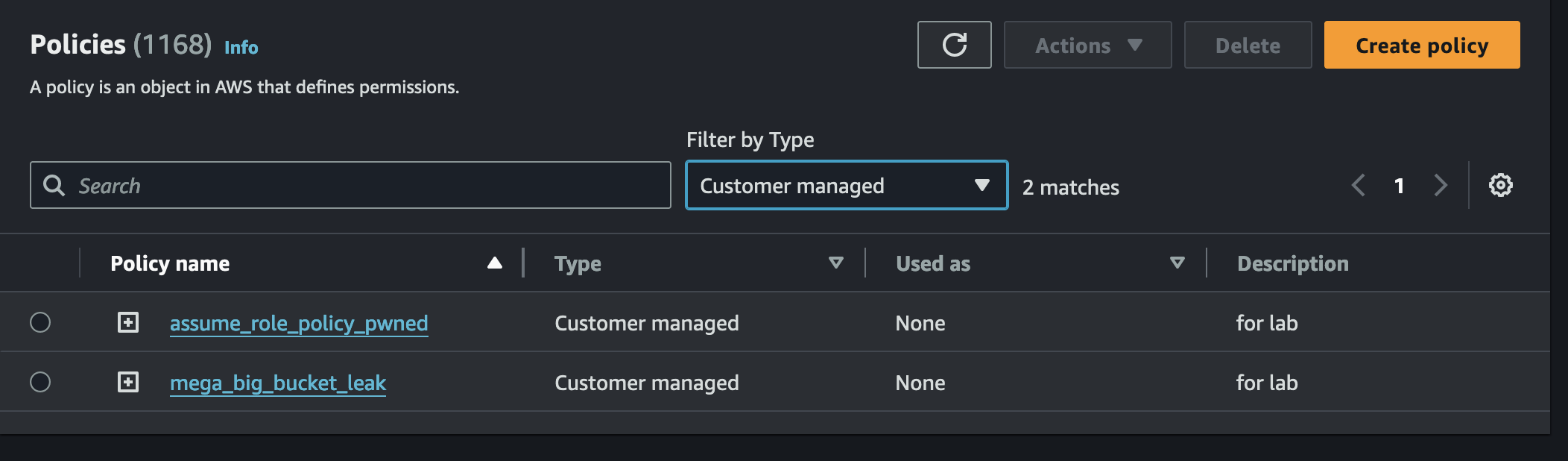
Part 2 - Rabbithole
Ok! I think this part will be the one that make most people confused because based on the lab after assigning these two policies to the user, like this:
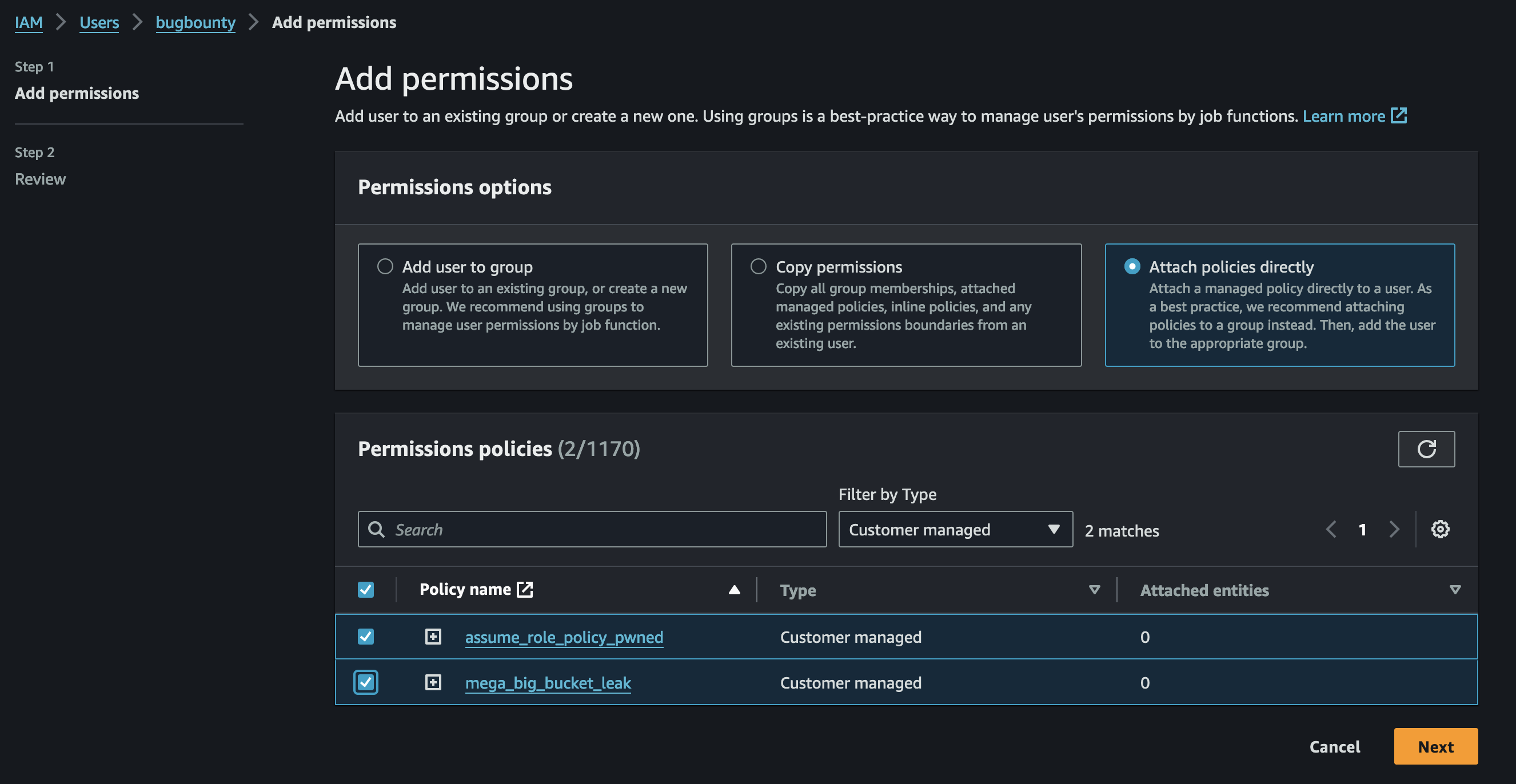
It will be sufficient but its not! if you try to run the s3-account-search program it will get the following error:
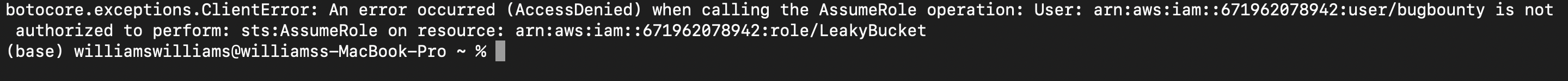
To resolve this issue we need to add one more key component which is “role” for S3 bucket
Part 3 - Resolve
Go to “role” section to create a new role for the user “leaky_user_bucket” for the policy inside the role we will used “custom trust policy” like this:
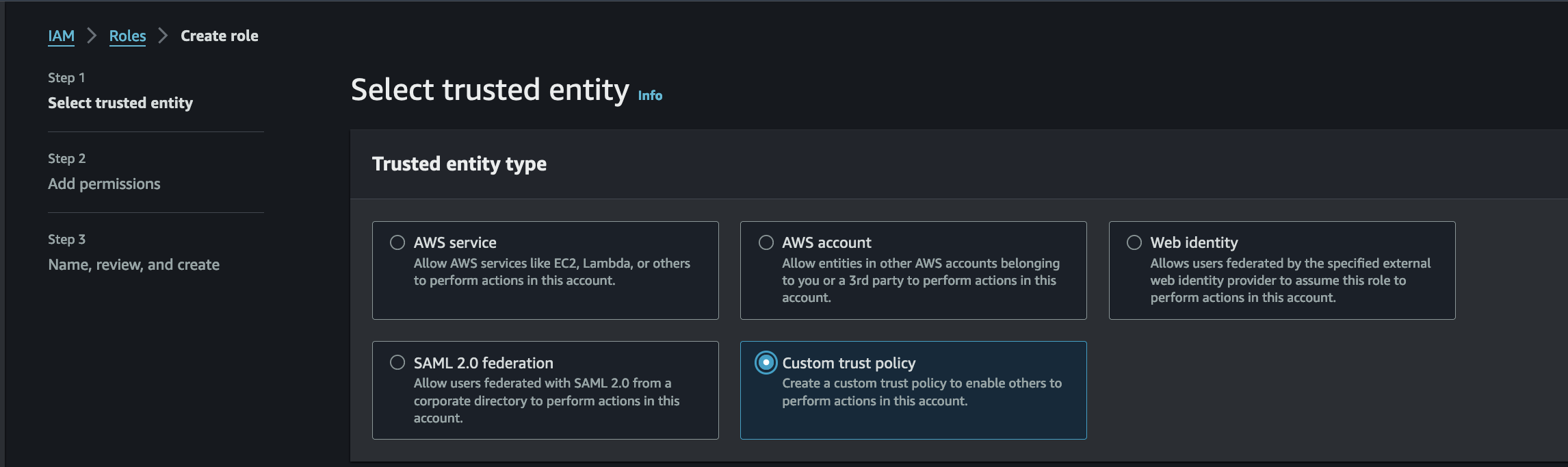
Put the following policy
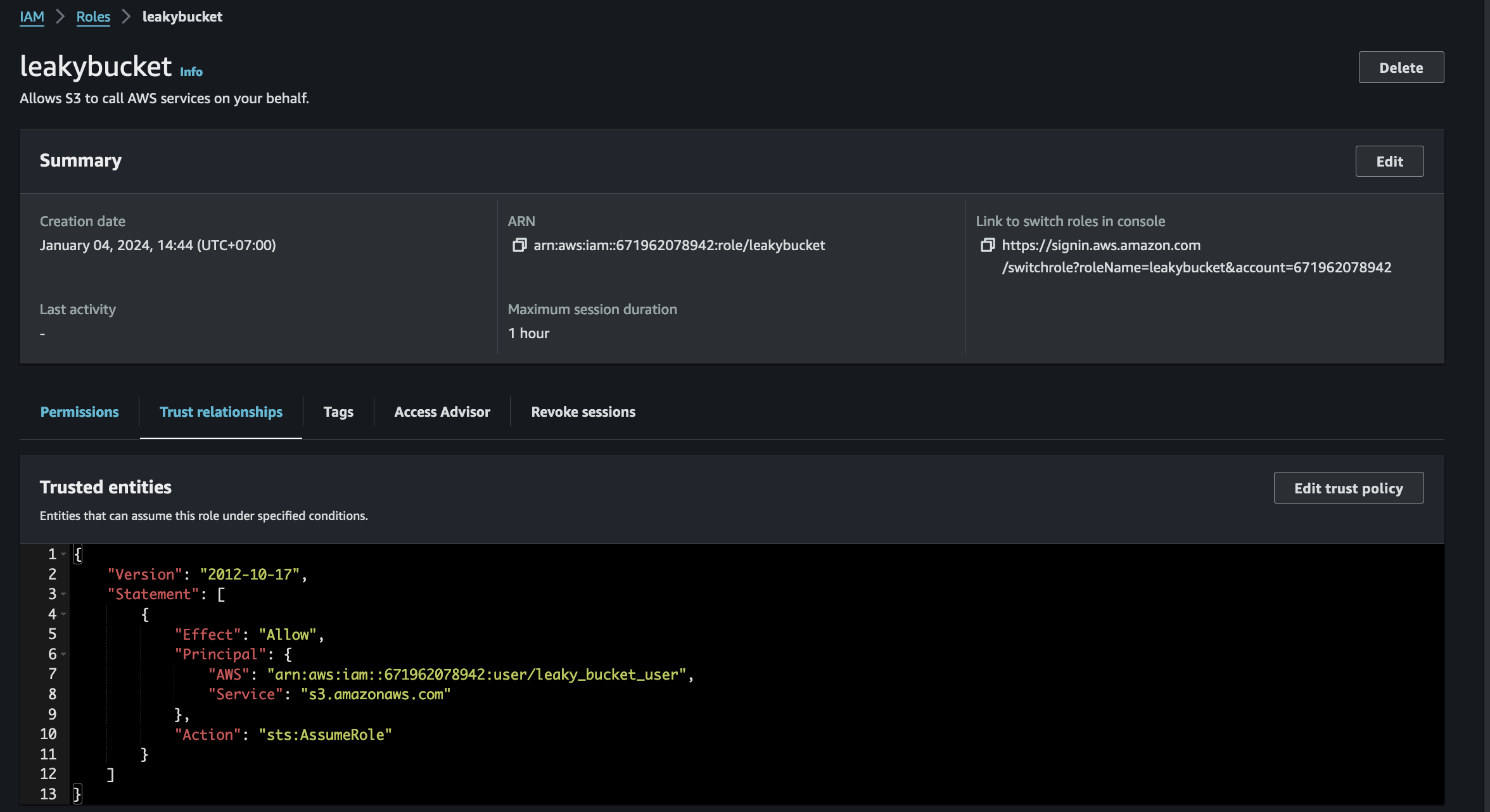
ok this is very important the name of the role need to be the same as the one you created in sts:AssumeRole if you don’t do it will give you the same error. Finally, you put the ARN of your aws account that you have created earlier in this case it will be the “leaky_user_bucket” by doing this we assing this role to our current user.
Then you can run the s3-account-search tool again and there you go it will give the account id:
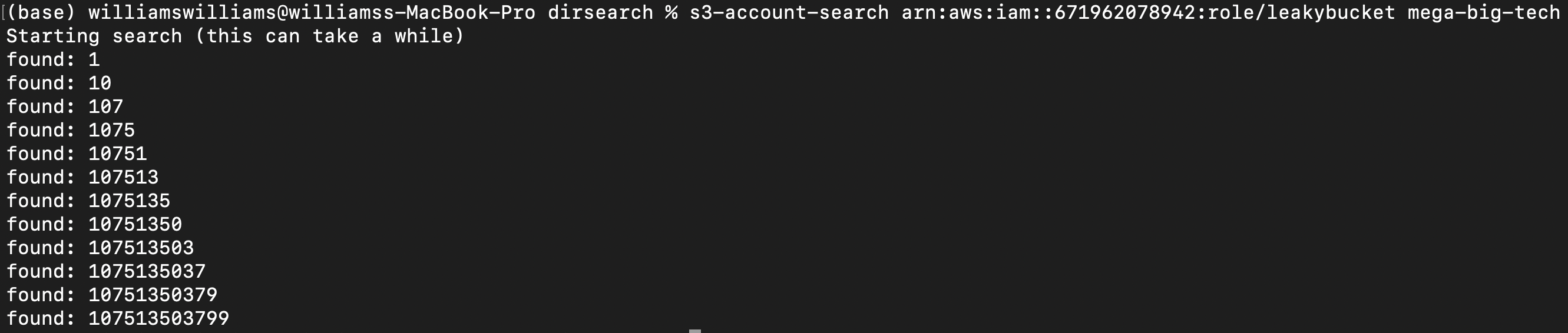
That’s all folks I hope you enjoy this post and see you next time!